
- Team has Over 100 Years Experience
- Managing Major Security Programs
- Consulting Engagements
- Developing New Security & Cryptographic Technology
- Authors of Numerous Books and Papers
- Team members have 10 Patents in Cryptography
- Taught Graduate Courses in Cryptography using Own Book
- Expert Witnesses in Cryptography
Previously Employed at:
SUPERDES™ GIGANTIC FAMILY OF ENCRYPTION ALGORITHMS
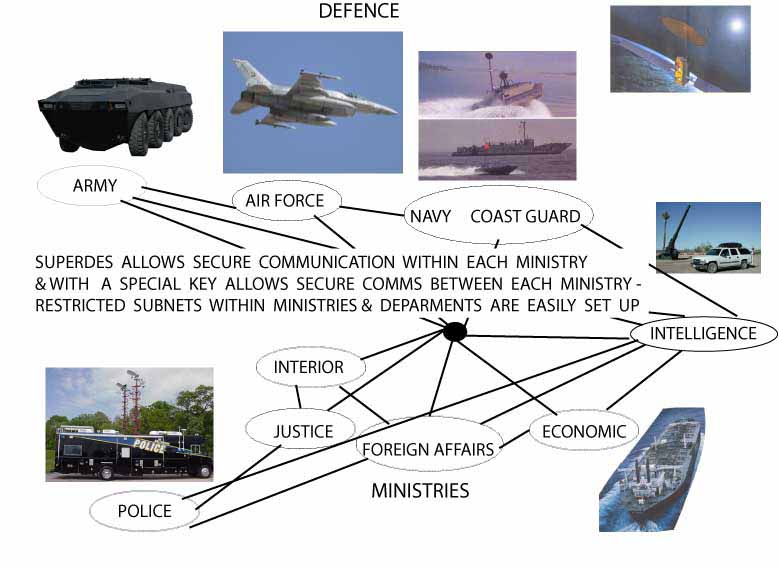
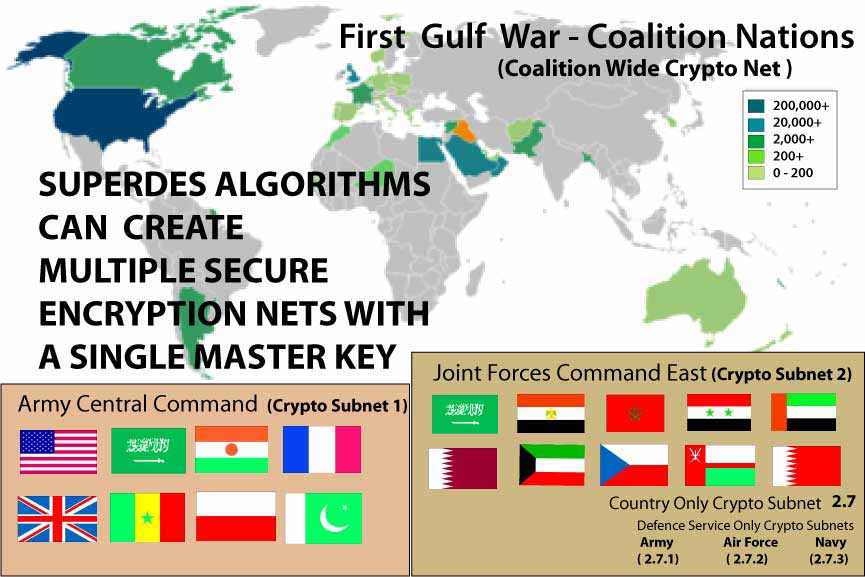
Graphics above show the benefits of a SUPERDES based Cryptographic Architecture with numerous coalition partners for multiple security and privacy levels but with interoperability at some basic level
- Patented SUPERDES™ Family of Symmetric Algorithms
- Unlimited Variations and Upgrades – Any Key Length
- Backward Compatible Modes with TDES / TDEA and DES / DEA
- Multiple Highly Secure Privacy Modes for Nets and Subnets but with a secure mode of Interoperability
- Implemented in Tactical Radios
- Non-exclusive license to Major High Tech Company MORE
- Extensive Research and Development in Cryptography
- Developed Innovative uses of Cryptography in SCADA, ICS and IOT Systems


