Risk is the likelihood of loss, damage, theft or compromise of critical assets of any form.
Senior management must evaluate and make high-level risk mitigating decisions on issues that cross traditional organization boundaries.
A major challenge to a comprehensive mitigation strategy is identifying relevant threats and vulnerabilities from:

CYBER
- Hacking for Information & Espionage
- Hacking for Ransom
- Hacking for Revenge or Ego
- Hacking to Disrupt or Damage for a Cause

PEOPLE
- Criminal Theft of Assets and Trade Secrets
- Malicious Insiders for Profit or Revenge
- Workplace Violence
- Riots and Violent Protests

NATURE
- Pandemics
- Floods
- Hurricanes
- Earthquakes
- Tornadoes
- Tsunamis
A common risk assessment framework enables senior management to make informed decisions involving risk in the context of current and future priorities, finite resources and global complexity.
The cycle of standard Risk Management Assessment (RMA) activities is illustrated below.
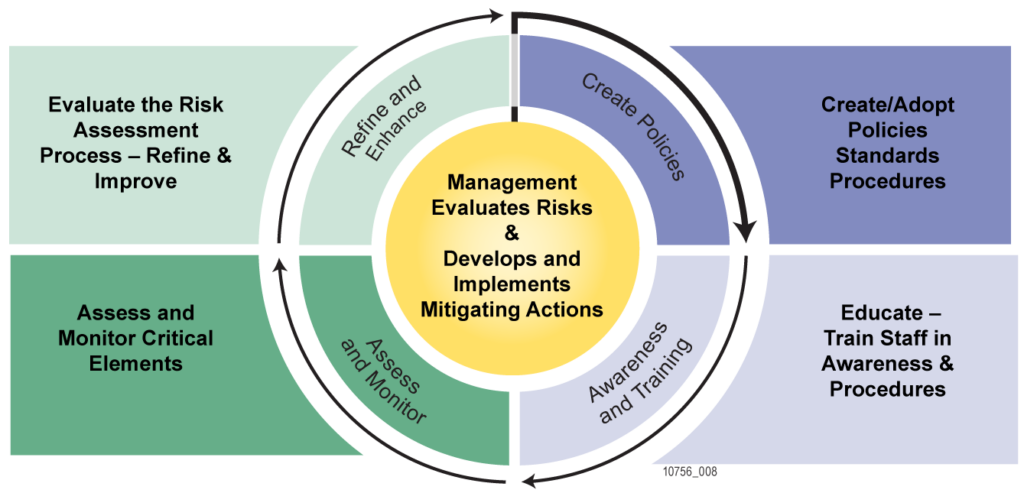
Risk Management Assessment (RMA) is a dynamic, iterative and harmonized set of processes for managing and assessing risk. Ideally it is consistent across various organizational elements since what one organization may evaluate as a high risk, another may identify as low risk because each used different criteria. The set of processes enable the identification and analysis of critical information and assets and to identify and consider their vulnerabilities and the current and potential threats facing them.
We Offer Training and Consulting in:
- Insider Threat Program Evaluation – Recommendations on Risks to Asset Value
- NIST Risk Management Framework
- NISPOM Tailored Security Plans – Based on Risk to Assets Plus Insider Threat
- Tailored Courses on Various Dimensions of Risk and Risk Standards & Guidelines


